Discover the ins and outs of XML injection attacks. This comprehensive article covers everything you need to know about XML injection vulnerabilities, their methodologies, and their prevention strategies.
Stay ahead of the curve and protect your systems from this malicious exploit.
Picture this: You’re in a virtual car driving along the information superhighway, minding your own business. Suddenly, an XML injection attack ambushes you like a cunning digital highwayman, aiming to manipulate and exploit your trusty XML files.
An XML injection vulnerability occurs when an attacker inserts malicious code into XML inputs, intending to disrupt the normal functionality of an application or gain unauthorized access to sensitive data.
When an application does not properly validate and sanitize user-supplied XML inputs, it becomes susceptible to these kinds of attacks.
These attacks can target various areas within the XML structure, such as element values, attributes, or namespaces.
By injecting specially crafted XML payloads, attackers can deceive the application into executing unintended actions or exposing confidential information.
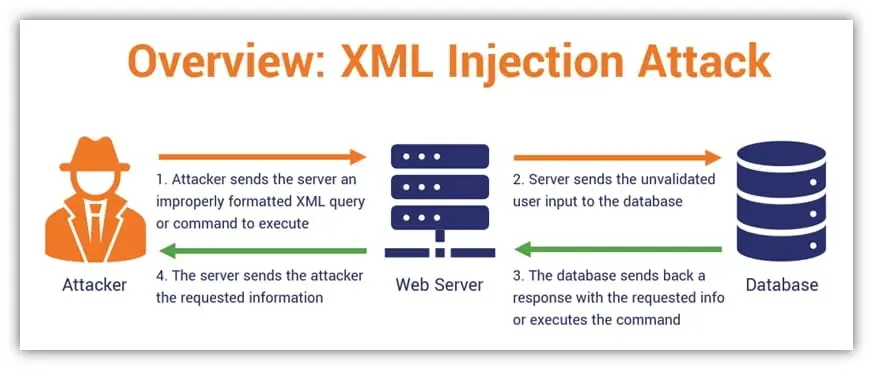
To illustrate the severity of an XML injection attack, let’s consider an example.
Imagine an online shopping application that uses XML to store product details.
If an attacker successfully injects malicious XML code, they could manipulate the XML tags, alter product prices, or even modify the entire structure of the XML document.
This could lead to incorrect pricing displayed to customers, unauthorized discounts applied, or even the exposure of sensitive customer data.
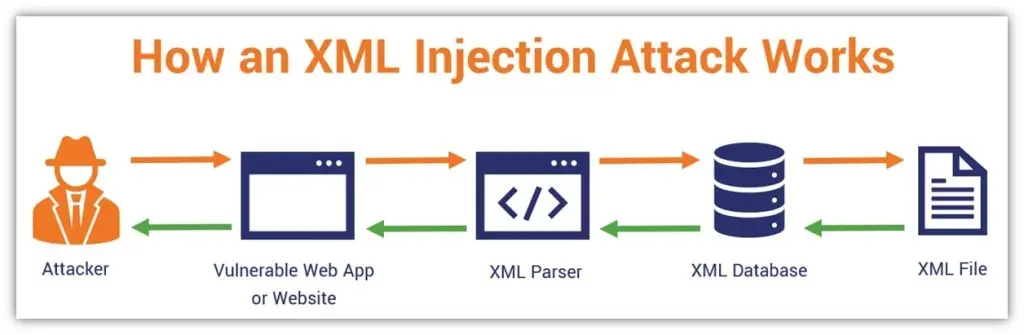
Let’s now peek behind the curtain and explore the methodology employed by XML injection attackers:
While XML injection and SQL injection share some similarities in terms of the potential risks they pose to web applications, they differ in their focus and exploitation techniques.
Let’s explore the key distinctions between these two formidable adversaries:
It revolves around manipulating XML inputs. Attackers leverage vulnerabilities in XML parsing and processing mechanisms to inject malicious code into XML files.
By exploiting these weaknesses, they can modify the XML structure, deceive the application, and execute unintended actions.
On the other hand, SQL injection targets web applications that utilize SQL databases.
Attackers manipulate user inputs to inject SQL queries or fragments into database queries.
These nefarious queries can tamper with database operations, extract sensitive information, or even modify the database structure.
While both attacks can lead to severe consequences, they require different techniques to exploit vulnerabilities. This threat focuses on crafting malicious XML payloads, while SQL injection relies on manipulating SQL queries through specially crafted input.
Now that you’re equipped with knowledge about these attacks, it’s time to steer clear of trouble.
Here are some effective prevention strategies to keep the XML injection highwayman at bay:
Remember, vigilance is the key to a secure digital journey. Stay informed, adopt best practices, and keep your guard up to protect your systems from the stealthy menace of XML injection attacks.
RDoS TL;DR Takeaways
Ransom DDoS (RDoS) attacks have emerged as a growing threat in 2023. Discover how these attacks work, the differences between Ransomware and DDoS, and effective measures to prevent and avoid Ransom DDoS attacks.
Ransom DDoS attacks, also known as RDoS, involve a malicious actor threatening to overwhelm an organization’s website or network with an enormous volume of traffic unless a ransom is paid.
The attackers typically demand payment in cryptocurrencies, such as Bitcoin, to remain anonymous and untraceable.
By exploiting vulnerabilities and leveraging botnets composed of compromised Internet of Things (IoT) devices, cybercriminals can execute devastating attacks.
Imagine your favorite website being bombarded with a massive surge of traffic, rendering it inaccessible to its users.
Now, the picture receiving a demand for payment to restore its normal functioning. This is the essence of a Ransom DDoS attack—a cyber siege aimed at crippling businesses and organizations.
While both Ransomware and DDoS attacks aim to disrupt and extort organizations, they differ in their methods and objectives.
Ransomware infiltrates a victim’s systems, encrypts valuable data, and demands a ransom to restore access.
On the other hand, DDoS attacks overwhelm a target’s network or website with a flood of traffic, rendering it inaccessible to legitimate users.
To better understand the distinction, let’s imagine a physical scenario: Ransomware is akin to a thief breaking into your office, locking away your files, and demanding a ransom to release them.
In contrast, DDoS attacks are like a crowd of protestors blocking the entrance to your office, preventing anyone from entering or leaving. While both scenarios cause disruption and demand payment, the methods employed differ significantly.
The rise of Ransom DDoS attacks necessitates proactive measures to safeguard your organization from potential devastation.
Here are some strategies to help you prevent or minimize the impact of RDoS attacks:
A: Ransom DDoS attacks have become increasingly common in recent years, with cybercriminals leveraging the ease of DDoS-as-a-Service platforms to execute these malicious campaigns.
A: While it can be challenging to trace RDoS attackers due to the anonymity provided by cryptocurrencies and the use of botnets, law enforcement agencies have made progress in attributing attacks to specific individuals or groups.
A: Any industry with an online presence can become a target of RDoS attacks.
However, sectors such as finance, healthcare, e-commerce, and gaming are particularly attractive to attackers due to their reliance on uninterrupted online services.
Ransom DDoS (RDoS) attacks have emerged as a significant menace in 2023, combining the disruptive power of DDoS with the extortion tactics of ransomware.
Understanding the workings of RDoS attacks, differentiating them from Ransomware, and implementing preventive measures are crucial for organizations aiming to protect their online presence.
By fortifying IT infrastructure, educating employees, implementing network monitoring, and developing comprehensive incident response plans, organizations can strengthen their defense against Ransom DDoS attacks.
Remember, prevention and preparedness are key in combating this evolving cyber threat.