Every minute your systems are down, money walks out the door. It’s not a hypothetical threat—it’s happening right now to businesses across Houston.
Recent research from BigPanda reveals that IT outages now cost an average of $14,056 per minute, with large enterprises paying up to $23,750 per minute. For context, a single two-hour outage could cost a mid-sized Houston business between $1.6 million and $2.8 million.
These aren’t just numbers. They represent missed sales, frustrated customers, and teams scrambling to put out fires instead of driving growth.
Houston’s technology landscape is booming. The region now employs over 158,000 tech professionals, with tech job postings growing 45.6% year-over-year—leading the entire nation. Companies like Apple, Tesla, and Nvidia are expanding operations here, creating a dynamic but complex digital ecosystem.
This rapid growth creates unique challenges. As businesses scale quickly to capitalize on Houston’s business-friendly environment, their technology infrastructure often struggles to keep pace. Legacy systems get stretched beyond capacity. Security gaps emerge. And when systems fail, the costs compound fast.
According to the 2025 State of Resilience report from Cockroach Labs, organizations now experience an average of 86 outages annually—that’s more than one per week. Perhaps most concerning: 70% of these outages take 60 minutes or longer to resolve.
Understanding the root causes helps prevent them. Here’s what typically triggers system failures:
Many Houston businesses run equipment that’s past its prime. Servers, network switches, and routers that exceed manufacturer support windows lack security patches and become increasingly unreliable. Research shows that nearly 70% of downtime stems from inadequate equipment maintenance or outdated systems.
Ransomware and cyber attacks can take operations offline for days or weeks. With 88% of small and medium businesses experiencing data breaches (compared to just 39% of large enterprises), smaller organizations face disproportionate risk. The average cost? Over $4.35 million per breach, according to IBM’s 2024 Cost of a Data Breach Report.
Accidental configuration changes, improper updates, or unauthorized access cause more disruptions than most executives realize. Without structured change management procedures and Identity and Access Management controls, these incidents become routine rather than exceptional.
Houston’s Gulf Coast location brings unique risks—hurricanes, flooding, and severe weather can all trigger extended outages for businesses without adequate disaster recovery planning.
Direct revenue loss is just the beginning. Queue-it’s downtime research found that companies with frequent outages pay up to 16 times more than organizations that maintain reliable systems.
Consider these additional impacts:
Prevention requires a proactive approach, not reactive firefighting. Here’s what works:
Modern monitoring tools detect anomalies before they become outages. LayerLogix’s managed IT services provide continuous network surveillance with real-time alerting, allowing technical teams to resolve issues during maintenance windows rather than during business hours.
The key is having expert support available when problems occur—not just during standard business hours. With round-the-clock Network Operations Center support, critical incidents get immediate attention regardless of timing.
Systematic maintenance schedules for security patches, firmware updates, and system health checks prevent the majority of unplanned outages. Organizations that implement proactive maintenance typically see a 60-80% reduction in downtime events.
Under flat-rate managed services agreements, businesses get comprehensive maintenance coverage without surprise emergency fees—making budgeting predictable and ensuring systems stay current.
Disaster recovery isn’t optional in Houston. Geographic redundancy, automated backups, and tested failover configurations protect against localized disasters common to the Gulf Coast region.
The difference between a minor inconvenience and a business-ending crisis often comes down to having systems in place before disaster strikes. LayerLogix’s disaster recovery solutions include automated backup systems and recovery protocols specifically designed for Texas businesses.
Modern cyber threats require multi-layered defense. This means more than just antivirus software—it requires endpoint detection and response (EDR), identity and access management, employee training, and continuous threat monitoring.
Virtual CISO services provide strategic security guidance without the cost of a full-time executive, helping mid-market companies implement enterprise-grade security controls.
As Houston businesses grow, their technology needs evolve. Planning infrastructure investments based on business growth projections—rather than reacting to crises—prevents the bottlenecks that lead to downtime.
Virtual CIO services offer strategic technology planning that aligns IT investments with business objectives, ensuring systems can handle tomorrow’s demands, not just today’s.
Here’s the reality: preventing downtime costs far less than recovering from it.
A comprehensive managed IT services agreement typically runs $100-$250 per user monthly, depending on service level. For a 50-person company, that’s $5,000-$12,500 monthly—or $60,000-$150,000 annually.
Now compare that to a single major outage: at $14,056 per minute, even a two-hour incident costs $1.68 million. One outage essentially pays for a decade of professional IT management.
Organizations that invest in comprehensive monitoring, maintenance, and security measures typically see:
If you’re still managing IT reactively—waiting for problems to happen before addressing them—you’re playing Russian roulette with your business continuity.
Start by understanding your current risk exposure:
Houston’s business environment offers tremendous opportunities for growth. But growth without a reliable technology infrastructure is building on quicksand.
The companies winning in Houston’s competitive market aren’t necessarily the biggest or best-funded—they’re the ones with systems that work when it matters most.
Need help assessing your downtime risk? LayerLogix provides complimentary IT assessments for Houston-area businesses. With over 30 years of collective experience and a proven MSP 3.0 approach integrating cybersecurity into every service layer, we help Texas businesses build resilient technology infrastructure.Learn more about protecting your business at layerlogix.com or read our article on cybersecurity services for Texas businesses.
Your IT team is drowning. Tickets pile up faster than they can be resolved. Security updates get postponed. Strategic projects never happen. And everyone’s just trying to keep the lights on.
Sound familiar?
You’re not alone. Research shows that average ticket volume has risen 16% since the pandemic, while 80% of small businesses have experienced IT-related downtime costing between $82,000 and $256,000 per incident. The gap between what businesses need from IT and what internal teams can deliver keeps widening.
Here are five concrete signs it’s time to bring in external expertise.
When support tickets accumulate faster than your team can close them, you’re not just facing an efficiency problem—you’re looking at a structural capacity issue.
The Reality: Help desk metrics research shows that steady ticket backlog growth signals problems with staffing, ticket routing, or support tools. When resolution rates consistently lag behind incoming requests, productivity losses compound across every department.
What It Costs: The average cost per support ticket ranges from $2.93 to $49.69, with an average of $15.56. But the real cost isn’t the ticket—it’s the 15.3 minutes of lost productivity employees experience daily due to tech issues, costing businesses $10.25 per employee per day.
The Fix: Managed service providers deliver scalable resources with specialized expertise across diverse technology domains. With tiered support and 24/7 monitoring capabilities, MSPs eliminate backlogs while maintaining consistent response times that stretched internal teams can’t achieve.
Organizations stuck in reactive mode see their IT teams consumed by urgent fixes rather than strategic initiatives. When your team spends more time responding to crises than preventing them, you’re losing ground.
The Pattern: Modern managed IT services use continuous network monitoring, automated alerting, and predictive analytics to identify vulnerabilities before they escalate. According to CSO Online, “burnout occurs when internal teams are overwhelmed by the sheer volume of operational tasks and can’t focus on strategic defense.”
The Impact: Neglecting routine maintenance—system updates, firmware upgrades, security patches—creates technical debt that eventually manifests as major failures. Organizations implementing proactive maintenance typically see 6a 0-80% reduction in unplanned downtime.
The Solution: LayerLogix’s MSP 3.0 approach embeds proactive monitoring as a standard service component. Flat-rate agreements include comprehensive maintenance windows for Office 365, cloud infrastructure, and on-premises hardware—ensuring systems stay optimized without disrupting operations.
Without robust Identity and Access Management frameworks and continuous security oversight, threats proliferate undetected. If your team lacks specialized security expertise, you’re exposed.
The Stakes: With 88% of small and medium businesses experiencing data breaches (compared to just 39% of large enterprises), smaller organizations face disproportionate risk. The average breach costs $4.88 million, but organizations without security AI and automation deployed pay $5.72 million—19% more.
The Gap: Many internal IT teams simply don’t have the bandwidth or expertise to implement comprehensive security controls. Research indicates that 72% of business leaders say their organizations lack the skills to fully implement AI and machine learning security tools.
The Answer: Virtual CISO services provide ongoing compliance oversight and risk management expertise. vCISO services cost 70-80% less than hiring a full-time CISO (typically $36,000-$60,000 annually versus $270,000-$425,000), while delivering enterprise-grade security governance. Organizations adopting vCISO services report up to 30% reduction in cybersecurity incidents within the first year.
Operational staff handling tactical IT issues rarely have the business perspective needed for strategic technology planning. Without executive-level IT leadership, technology investments happen reactively rather than strategically.
The Problem: Mid-market companies often operate without senior IT leadership, leaving critical technology decisions to staff who may lack strategic business acumen. When IT teams focus exclusively on immediate operational needs—workstation deployments, email migrations, urgent fixes—there’s no coherent strategy guiding investments toward business outcomes.
The Evidence: According to TechMagic research, the average CISO tenure is just 26 months, and recruitment cycles can span years. For growing businesses, that gap in strategic leadership creates real risk.
The Alternative: Virtual CIO services provide quarterly business reviews that align IT initiatives with growth objectives and ROI targets. This strategic oversight transforms IT from a cost center into a competitive advantage—without the substantial cost of full-time executive hires. Over 60% of mid-sized businesses plan to adopt these services within the next year.
Opening new locations, integrating remote workers, or scaling operations quickly can overwhelm internal IT resources sized for smaller, centralized operations. Rapid expansion often outpaces infrastructure capability.
The Challenge: Maintaining consistent IT services across multiple locations typically exceeds internal team capabilities, especially during rapid growth. IDC research found that 80% of small businesses have suffered IT-related downtime, costing between $82,000 and $256,000 per incident.
The Complexity: Cloud migrations, Office 365 adoption, and multi-location networking require sophisticated governance, data protection, and change management capabilities that stretched internal teams often lack.
The Path Forward: Managed services models provide flexible scaling that adjusts resources to match business expansion without requiring significant capital investments or extended hiring processes. With offices across The Woodlands, Houston, Dallas, and Round Rock, providers like LayerLogix deliver on-site service capabilities that support growth while maintaining security standards.
Contrary to common misconceptions, bringing in managed services doesn’t mean eliminating your internal team or surrendering control. It means a strategic partnership.
If you recognized your organization in three or more of these signs, it’s time for an honest assessment of your IT capabilities versus your business needs.
Start with these steps:
The companies winning in competitive markets aren’t necessarily those with the biggest IT budgets—they’re the ones with IT infrastructure that actually supports growth rather than constraining it.
Ready to assess your IT readiness? LayerLogix offers complimentary IT assessments for Texas businesses. With over 30 years of collective experience and a proven MSP 3.0 approach, we help businesses build scalable, secure technology infrastructure.Learn more at layerlogix.com or explore our article on defending against cyber threats.
Your finance team hates surprises. So does your CFO. And nothing creates budget chaos quite like unpredictable IT expenses.
Emergency server repair? $3,500. After-hours support call? $350 per hour. Security incident response? Better not ask.
This is the reality of break-fix IT support—and why successful MSP partnerships can reduce IT costs by 25-45% compared to reactive models. Flat-rate IT support replaces budget volatility with predictable monthly costs while delivering comprehensive service coverage that actually prevents problems instead of just fixing them.
Here’s why Texas companies are making the switch.
Break-fix IT operates on a simple premise: you pay when something breaks. It sounds reasonable—why pay for IT when everything’s working?
Because everything’s never working for long.
The True Cost: Hourly rates for break-fix services range from $75 to $200, with emergency response reaching $300+ per hour. But the real problem isn’t the hourly rate—it’s the reactive model itself. System outages during break-fix repairs cost $5,600 to $9,000 per minute, making every incident exponentially more expensive than proactive prevention.
The Hidden Costs: Break-fix creates perverse incentives. Your IT vendor only makes money when things break, so there’s little motivation to prevent problems. You’re essentially paying someone to wait for disasters rather than prevent them.
According to CompTIA research, 50% of companies saved 1-24% in IT costs through managed services, while 33% saved 25-49%, and 13% saved more than 50%. The reason? Prevention costs less than crisis management.
Flat-rate IT support operates on a subscription model—you pay a fixed monthly fee for comprehensive managed services. But the value isn’t just cost predictability; it’s the shift from reactive to proactive management.
Typical Coverage: Per-user pricing ranges from $125 to $220 per user monthly, depending on service level. This includes:
The Math Works: For a 50-person company at $150 per user monthly, that’s $7,500—or $90,000 annually. Compare that to a single full-time IT professional ($80,000-$120,000 salary plus benefits) who can’t provide 24/7 coverage or specialized expertise across security, cloud, and compliance.
Budget predictability matters, but the real ROI comes from operational improvements that flat-rate models enable.
Not all flat-rate models work the same way. Understanding the differences helps you select the right structure for your business.
Not every flat-rate agreement delivers equal value. Watch for these potential issues:
For businesses considering the switch from break-fix or in-house IT to flat-rate managed services, building the business case requires comparing total cost of ownership.
Current State Analysis:
Future State Projection:
Research shows that successful MSP partnerships reduce overall IT costs by 25-45% while significantly improving security posture and operational reliability.
Texas businesses benefit from a competitive managed services market with providers who understand regional challenges—from Gulf Coast disaster recovery planning to industry-specific compliance requirements in healthcare, manufacturing, and energy sectors.
LayerLogix’s approach combines flat-rate predictability with comprehensive service delivery tailored to Texas business environments. With over 30 years of collective experience and offices across The Woodlands, Houston, Dallas, and Round Rock, we deliver enterprise-level technology management with the local presence that matters when you need on-site support.
Our MSP 3.0 model integrates cybersecurity, compliance, and strategic leadership as core services—not expensive add-ons. You get 24/7 monitoring, proactive maintenance, virtual CIO/CISO expertise, and on-site support capabilities under one predictable monthly rate.
Flat-rate IT support isn’t just about budget predictability—though that matters. It’s about shifting from crisis management to strategic technology partnership.
The companies thriving in Texas’s competitive business environment aren’t those spending the most on IT. They’re the ones with technology infrastructure that works reliably, scales efficiently, and supports growth objectives instead of constraining them.
When your finance team can budget IT accurately, your security posture meets enterprise standards, and your technology actually enables competitive advantage rather than creating emergencies—that’s when flat-rate pricing proves its value.
Ready to eliminate IT budget surprises? LayerLogix offers complimentary IT assessments for Texas businesses. Discover how flat-rate managed services can reduce costs while improving reliability and security.Learn more at layerlogix.com or explore how we help construction companies scale technology infrastructure efficiently.
Basic antivirus solutions have become dangerously inadequate protection against sophisticated cyber attacks. A robust multi-layered cybersecurity strategy provides comprehensive defense-in-depth, detecting and neutralizing threats at every stage of their intrusion attempt.
With over 30 years of collective experience safeguarding Texas businesses, LayerLogix delivers 24/7 support, continuous proactive monitoring, and responsive on-site service across The Woodlands, Houston, Dallas, and Round Rock.
As your “external IT team that’s so integrated, you’ll forget we don’t work there,” we seamlessly blend infrastructure management, Office 365 governance, advanced cloud security, and transparent flat-rate pricing into a holistic security approach. This integrated model ensures business continuity through disruptions and maximizes technology ROI.
Ransomware attacks have transformed from opportunistic nuisances into targeted, enterprise-crippling threats, surging by 92% in 2022 with average payments exceeding $800,000 according to the IBM Cost of a Data Breach Report. The Colonial Pipeline incident demonstrates the operational devastation possible, having disrupted 45% of East Coast fuel distribution and causing widespread supply chain chaos. For Texas businesses—particularly in energy, healthcare, and manufacturing sectors—similar attacks could result in production stoppages costing $100,000+ per hour in lost revenue and recovery expenses.
Legacy antivirus products rely primarily on signature-based detection methods, scanning files against known malware databases. This approach fails to identify fileless malware, polymorphic threats, and zero-day exploits that don’t match existing signatures. Modern attackers exploit these blind spots, maintaining persistence within networks—Mandiant reports an average dwell time of 243 days—silently harvesting credentials and mapping networks before launching destructive payloads. During this extensive reconnaissance period, traditional antivirus software remains completely blind to their presence.
According to the National Cybersecurity Alliance, 60% of small to mid-sized businesses close within six months of a significant cyber attack. For Texas enterprises, inadequate security posture creates existential business risk. The average cost of a data breach now exceeds $4.45 million, with heavily regulated industries like healthcare ($10.93M) and financial services ($9.48M) facing even steeper consequences. These figures demonstrate why piecemeal security approaches centered solely on antivirus protection no longer suffice in protecting critical business assets.
Modern NGFWs extend far beyond traditional firewalls, providing deep packet inspection, application-aware filtering, and integrated threat intelligence capabilities. LayerLogix deploys enterprise-grade firewall solutions that examine packet contents rather than just headers, identifying and blocking malicious traffic patterns before they enter your network. For multi-location Texas businesses with offices in Houston, Dallas, and beyond, we implement consistent security policies through centralized management, eliminating dangerous security gaps between sites.
As web-based threats proliferate, Secure Web Gateways provide essential protection by inspecting SSL/TLS-encrypted traffic and enforcing granular URL filtering policies. According to Gartner, organizations implementing SWGs reduce web-based threats by up to 70%, protecting both corporate and remote users. LayerLogix configures these gateways with industry-specific policies, blocking access to malicious sites and preventing sensitive data exfiltration through cloud storage or unauthorized channels.
Network segmentation creates logical boundaries between systems, limiting attackers’ ability to move laterally through your environment. For Texas manufacturing clients, our segmentation strategies isolate operational technology (OT) networks from corporate IT, preventing ransomware from compromising production equipment. Similarly, healthcare clients benefit from PHI isolation that contains potential exposures and simplifies compliance verification. This approach transforms a flat, easily traversable network into a compartmentalized environment where breaches remain contained and detectable.
Modern EDR solutions have evolved far beyond traditional antivirus capabilities, continuously monitoring endpoint behaviors including process execution, memory manipulation, and network communications. When LayerLogix deploys EDR across your environment, we establish behavioral baselines and implement automated response workflows that instantly isolate compromised devices upon detecting anomalous activities—such as unusual PowerShell execution or registry modifications. This real-time containment prevents lateral movement and limits the potential damage scope.
Effective IAM forms a critical security layer by enforcing the principle of least privilege, implementing multi-factor authentication, and centralizing directory services. MFA alone blocks over 99.9% of automated credential attacks according to Microsoft research. For Texas businesses leveraging Office 365 and hybrid cloud services, LayerLogix implements comprehensive identity governance, including Privileged Access Management (PAM) that secures administrative accounts, enforces just-in-time access, and records all privileged sessions for audit and compliance verification.
The Zero Trust security model operates on the principle “never trust, always verify,” requiring continuous validation of every user and device attempting to access resources, regardless of location. For organizations with distributed workforces across Houston, Dallas, and Round Rock, this approach is particularly valuable in securing remote access to critical data and applications. LayerLogix designs Zero Trust frameworks that enforce strict authentication, authorization, and encryption requirements—reducing attack surface and preventing credential-based attacks that easily bypass traditional perimeter defenses.
LayerLogix’s Security Operations Center operates around the clock, ingesting and correlating log data from endpoints, firewalls, cloud platforms, and Office 365 environments using advanced SIEM technology. This continuous monitoring enables us to identify threat patterns across thousands of daily events, delivering a Mean Time to Detection (MTTD) under 15 minutes—critical when containment speed directly impacts breach costs. Unlike reactive approaches that discover breaches weeks or months later, our 24/7 vigilance ensures Texas businesses maintain comprehensive protection at all hours.
Moving beyond alert-driven security, LayerLogix employs specialized threat hunting teams that proactively search for Indicators of Compromise (IoCs) within client environments. Using both commercial and open-source intelligence feeds, our hunters identify dormant malware, detect insider threats, and discover advanced persistent attacks before damage occurs. For critical infrastructure clients in The Woodlands and Houston energy sectors, this proactive stance provides early warning of sophisticated threats that would remain invisible to traditional security tools.
When security incidents occur, LayerLogix executes predefined response playbooks tailored to your organization’s specific requirements. Our incident response teams combine remote investigation capabilities with on-site expertise across Texas locations, ensuring rapid containment and eradication of threats. Response activities include forensic evidence collection, malware removal, vulnerability remediation, and detailed reporting for compliance and insurance purposes. This structured approach minimizes business disruption and reduces recovery timelines from weeks to days.
Growing Texas businesses often lack dedicated IT leadership to align technology investments with business objectives. LayerLogix’s virtual CIO/CISO services bridge this gap by providing fractional executive expertise at a fraction of full-time salary costs. Our technology roadmapping process identifies strategic priorities, creates phased implementation plans, and develops realistic budgets that maximize security ROI while supporting operational goals. This approach ensures every dollar invested in cybersecurity delivers measurable business value through risk reduction and compliance achievement.
Texas organizations face complex regulatory landscapes—from HIPAA in healthcare to NIST for government contractors and PCI DSS for retail. Our virtual CISO team develops tailored compliance frameworks, including documented policies, incident response procedures, and regular audit schedules. For healthcare clients in Houston and Dallas, we implement specialized controls for PHI protection, while manufacturing clients benefit from supply chain security assessments and OT-specific controls. These frameworks transform compliance from a checkbox exercise into a strategic advantage that builds customer trust.
Recruiting a qualified in-house CISO in Texas commands salaries exceeding $200,000 annually plus benefits, placing dedicated security leadership beyond reach for many mid-market companies. LayerLogix’s virtual CISO services start at $3,500 per month, delivering quarterly risk assessments, vendor security reviews, and executive-level reporting that keeps leadership informed of security posture and emerging threats. This model provides enterprise-grade security guidance without the overhead, making strategic expertise accessible to growing Texas businesses that need it most.
As Texas businesses accelerate digital transformation initiatives, LayerLogix architects design secure hybrid cloud environments on Azure and AWS platforms, implementing proper encryption, access controls, and security monitoring. By strictly following the AWS Shared Responsibility Model, we address 80% of cloud breaches resulting from customer-side misconfigurations. Our methodical approach to cloud migration includes workload assessment, security integration, and continuous compliance verification—ensuring that cloud adoption enhances rather than compromises your security posture.
Microsoft 365 deployments create significant security challenges without proper governance. LayerLogix implements comprehensive controls, including retention policies, Data Loss Prevention (DLP) rules, and appropriate encryption for Exchange, Teams, and SharePoint environments. Our monthly security posture assessments identify configuration drift and security gaps, while automated alerts flag anomalous access patterns that might indicate account compromise. This governance framework ensures Texas businesses maximize productivity benefits while maintaining data security and compliance with industry regulations.
Disasters—whether natural, technical, or security-related—can cripple unprepared organizations. LayerLogix develops custom Disaster Recovery (DR) plans with clearly defined Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) aligned with business priorities. Our immutable backup solutions create tamper-proof recovery points that protect against ransomware targeting backup infrastructure, while quarterly testing validates recovery procedures under realistic conditions. Typical DR engagements range from $2,000 to $7,500 per month, delivering exceptional ROI by preventing downtime costs averaging $5,600 per minute for mid-sized enterprises.
Under our forward-thinking MSP 3.0 model, comprehensive cybersecurity isn’t an expensive add-on—it’s a standard component of our service offerings. LayerLogix’s transparent flat-rate plans, ranging from $1,200 to $5,000 per month based on environment complexity, include complete infrastructure management, helpdesk support, proactive monitoring, security controls, and data protection. This predictable pricing structure eliminates budget surprises and scaling friction, allowing Texas businesses to align IT investments with growth objectives. For organizations previously burned by unexpected hourly billing, this approach represents a welcome shift toward strategic partnership.
Grounded in integrity, transparency, and exceptional stewardship, LayerLogix builds lasting relationships based on mutual trust and shared success. Our faith-based approach influences every aspect of client interaction—from honest needs assessments to transparent recommendations that prioritize your interests above short-term gains. For Texas businesses seeking technology partners they can truly trust, this values-driven culture ensures we treat your infrastructure, data, and security with the same care and diligence we apply to our own operations.
With headquarters in The Woodlands and offices serving Houston, Dallas, and Round Rock, LayerLogix possesses a deep understanding of regional business environments, industry regulations, and local threat landscapes. Our engineers deliver on-site support when needed, whether deploying secure infrastructure for a Houston energy firm, conducting tabletop exercises for a Dallas healthcare provider, or implementing multi-site networking for retail clients across Texas. As your external IT team that’s so integrated you’ll forget we don’t work there, we combine local presence with deep technical expertise to address Texas-specific business challenges across diverse industries.
As cyber threats continue to evolve in sophistication and impact, basic antivirus protection has become woefully insufficient for protecting modern businesses. A comprehensive multi-layered cybersecurity strategy represents not just best practice but a business necessity for organizations seeking to safeguard operations, reputation, and bottom line. By implementing defense-in-depth through advanced perimeter controls, endpoint protection, identity management, proactive 24/7 monitoring, cloud governance, and strategic virtual CIO/CISO leadership, LayerLogix delivers enterprise-grade security tailored specifically for Texas businesses.
Our MSP 3.0 approach—backed by 30+ years of industry experience, 24/7 support capabilities, on-site expertise across The Woodlands, Houston, Dallas, and Round Rock, and transparent flat-rate pricing—transforms cybersecurity from a technical expense into a strategic business enabler. Built on integrity and stewardship, our partnership model ensures your organization benefits from comprehensive protection without management burden or budget unpredictability.
Ready to strengthen your security posture with a true multi-layered cybersecurity strategy? Contact LayerLogix today at 281-607-5040 for a complimentary security assessment and discover how our integrated approach can protect your Texas business against evolving threats while delivering measurable ROI and peace of mind.
Every unexpected IT outage chips away at revenue, productivity, and customer confidence. With 24/7 IT monitoring at the core of proactive IT support, businesses across The Woodlands, Houston, Dallas, and Round Rock can anticipate and remediate issues before they escalate into costly downtime. LayerLogix—your external IT team that’s so integrated, you’ll forget we don’t work there—combines over 30 years of collective experience, MSP 3.0 positioning, Christian business values, and virtual CIO/CISO leadership to deliver 24/7 support, proactive monitoring, on-site service, and flat-rate managed services that keep operations humming.
Industry research consistently shows that unplanned downtime costs mid-sized organizations substantial amounts per incident. While exact figures vary by sector and company size, a single hour-long outage at a Dallas manufacturing plant can quickly escalate into hundreds of thousands of dollars in lost production, emergency repairs, and service level agreement penalties.
When Office 365, cloud databases, or internal networks go offline, employees in Houston clinics or Round Rock financial firms lose access to critical applications, stalling workflows and frustrating customers. Research indicates that approximately 30% of clients will reconsider vendor relationships after repeated service failures, making reputation recovery both lengthy and costly.
For healthcare providers, HIPAA mandates continuous access to electronic health records; downtime violations can trigger significant penalties. The HHS Office for Civil Rights enforcement examples demonstrate how serious these violations can become, with fines reaching substantial amounts annually. Financial services face SEC and FINRA audits, while manufacturing firms risk EPA sanctions if environmental controls fail. Proactive monitoring reduces compliance gaps by ensuring critical systems remain online.
Effective 24/7 IT monitoring gathers telemetry from servers, network devices, Office 365 tenants, and multi-cloud workloads. LayerLogix uses synthetic transactions and agent-based metrics to spot latency spikes and resource bottlenecks before they impact users.
Aligned with NIST’s continuous monitoring standards, automated playbooks can restart services, trigger failovers, or isolate compromised endpoints in seconds—dramatically reducing mean time to resolution and averting major outages. NIST Special Publication 800-137 emphasizes how automation enables rapid detection and response to both security and operational events.
Proactive monitoring shines brightest when paired with strategic oversight. LayerLogix’s virtual CIO services create IT roadmaps, budget forecasts, and migration strategies. Virtual CISO guidance ensures that cybersecurity frameworks, IAM policies, and threat response plans evolve alongside emerging risks—without the overhead of full-time executive hires.
Unlike remote-only providers, LayerLogix maintains certified engineers in The Woodlands, Houston, Dallas, and Round Rock. Under a flat-rate agreement, our team is dispatched onsite whenever hardware-level issues or physical interventions are required—no surprise fees, no delays.
Budget certainty matters for growth-focused Texas leaders. LayerLogix’s flat-rate managed services include 24/7 IT monitoring, proactive maintenance, on-site support, and vCIO/CISO consultations—eliminating break-fix invoices and aligning incentives around prevention.
From Office 365 governance and cloud migrations to IAM, cybersecurity, disaster recovery, and business continuity planning, LayerLogix delivers end-to-end services that eliminate vendor sprawl. Our MSP 3.0 model embeds security as standard, ensuring holistic protection and seamless support.
Office 365 underpins email, collaboration, and document management for most mid-market firms. LayerLogix continuously monitors mailbox health, SharePoint performance, and Teams connectivity while enforcing multi-factor authentication and conditional access policies to guard against account compromise.
Whether your workloads live in Azure, AWS, or on-premises data centers, LayerLogix unifies monitoring across platforms. Automated alerts for CPU spikes, storage saturation, and backup failures feed into remediation workflows that auto-scale resources or shift workloads to redundant environments.
Unauthorized access often precedes data breaches. Continuous IAM monitoring flags anomalous login patterns and privilege escalations, integrating with Microsoft’s security APIs and third-party threat feeds to lock down compromised accounts before damage occurs.
Backups must be validated. LayerLogix automates integrity checks for on-premises servers, Office 365 mailboxes, and cloud data stores to ensure recovery points meet defined RPO/RTO metrics. Scheduled failover drills confirm that critical applications—EHR systems in Houston clinics or SCADA controls in Woodlands plants—can switch to secondary sites seamlessly.
Semi-annual DR exercises simulate power outages, ransomware attacks, and natural disasters. These drills refine runbooks, test vendor coordination, and ensure staff readiness, so that when a real event strikes, recovery is swift and structured.
Uptime Institute research indicates that proactive maintenance can significantly reduce unplanned downtime by implementing early detection and preventive measures. When uptime directly preserves revenue streams and customer satisfaction, the ROI on 24/7 IT monitoring and managed services becomes unmistakable.
The shift to hybrid work models has expanded the attack surface and increased complexity. LayerLogix monitors VPN connections, endpoint security, and cloud application performance to ensure remote workers maintain productivity without compromising security.
Regulated industries require detailed audit trails and compliance reporting. Continuous monitoring generates the documentation needed for regulatory audits while ensuring systems meet industry standards for data protection and availability.
Cybercriminals continually evolve their tactics. Advanced monitoring incorporates behavioral analytics and threat intelligence to identify zero-day attacks, insider threats, and sophisticated social engineering attempts that traditional security tools might miss.
LayerLogix’s faith-based approach fosters integrity, transparency, and service above self. Our Christian business values resonate with Texas executives who seek ethical stewardship of their IT investments and long-term partnerships built on trust.
Deep Texas market knowledge means faster response times and solutions tailored to regional business climates—from Houston’s healthcare sector to Dallas’s financial services hub and Round Rock’s tech corridor.
Proactive IT monitoring is an evolving journey. Quarterly business reviews deliver dashboard insights, incident trend analyses, and strategic recommendations, ensuring your proactive support model scales with your growth objectives.
Every successful monitoring deployment begins with a comprehensive assessment of existing infrastructure, identifying critical systems, performance baselines, and potential failure points. LayerLogix conducts thorough network audits to establish monitoring priorities aligned with business objectives.
Implementation follows a phased approach that minimizes disruption while maximizing coverage. Staff training ensures internal teams understand alert procedures and can collaborate effectively with monitoring specialists during incident response.
As businesses grow and technology evolves, monitoring strategies must adapt. Regular reviews and optimization ensure monitoring coverage expands with new systems while maintaining optimal performance and cost-effectiveness.
IT insecurities—vulnerabilities within a company’s information technology systems—pose significant risks to businesses of all sizes. From data breaches to cyber-attacks, these insecurities can lead to financial loss, reputational damage, and operational disruption. Recognizing common IT insecurities and implementing proactive defenses can help businesses safeguard their information, ensure system integrity, and maintain customer trust.
By understanding these common IT insecurities and taking proactive steps, businesses can fortify their defenses, protect sensitive data, and minimize the impact of security threats. In today’s interconnected world, prioritizing IT security is no longer optional—it’s essential for the success and longevity of any organization.
In today’s digital world, a stable network connection isn’t just a luxury—it’s a necessity. Whether you’re working remotely, streaming your favorite shows, or staying connected with loved ones, a reliable internet connection keeps your life running smoothly. Yet, network issues can arise unexpectedly, causing frustration and disrupting your daily routine.
This comprehensive guide is designed to help you troubleshoot common network connection problems and understand their root causes. We’ll provide step-by-step solutions, helpful tips, and answers to frequently asked questions. By the end of this guide, you’ll be empowered to tackle network issues confidently and maintain a seamless online experience.
A network is a collection of computers, servers, mobile devices, or other electronic devices connected to share data and resources. Think of it as a digital highway system, where information travels between devices, enabling communication and collaboration.
Networks are essential for:
Understanding the different types of networks helps in identifying and resolving issues effectively.
Familiarizing yourself with network hardware can simplify troubleshooting.
Network problems can manifest in various ways. Recognizing the symptoms is the first step toward a solution.
Symptoms:
Possible Causes:
Symptoms:
Possible Causes:
Symptoms:
Possible Causes:
Symptoms:
Possible Causes:
Symptoms:
Possible Causes:
A systematic approach ensures you cover all bases and identify the root cause effectively.
Action Steps:
Why It Matters:
Physical issues are often overlooked but can be the simplest to fix. A loose cable or unplugged device can disrupt your entire network.
Action Steps:
Why It Matters:
Restarting clears temporary glitches and resets network configurations, often resolving connectivity issues.
Action Steps:
Why It Matters:
Outdated firmware or drivers can cause compatibility issues and security vulnerabilities.
Action Steps:
ipconfig /flushdnsWhy It Matters:
Incorrect settings can prevent devices from communicating with the network or accessing the internet.
Action Steps:
ping 8.8.8.8 to test connectivity to Google’s DNS server.tracert [website] (Windows) or traceroute [website] (Mac/Linux) to identify where the connection fails.netsh winsock reset netsh int ip resetWhy It Matters:
These tools help diagnose deeper issues beyond basic connectivity, pinpointing where data transmission fails.
Identifying the underlying cause prevents recurring problems.
Indicators:
Solutions:
Indicators:
Solutions:
Indicators:
Solutions:
Indicators:
Solutions:
| Problem | Possible Cause | Solution |
|---|---|---|
| Can’t connect to Wi-Fi | Incorrect password | Re-enter password; reset network settings; reboot router. |
| Slow internet speed | Bandwidth congestion | Limit device usage; upgrade internet plan; use wired connections for critical devices. |
| Wi-Fi signal weak in specific areas | Router placement | Move router; use Wi-Fi extenders or mesh network systems. |
| Frequent disconnections | Hardware issues | Replace or update router/modem; check cables; ensure firmware is up-to-date. |
| Certain websites not loading | DNS or firewall issues | Change DNS settings; adjust firewall settings; clear browser cache. |
| Devices can’t see each other on the network | Network discovery disabled | Enable network sharing settings; ensure devices are on the same network and workgroup. |
| Printer not connecting to network | Driver issues or network settings | Update printer drivers; check network configurations; ensure printer is on the same network. |
| VPN connection drops frequently | Network instability | Update VPN client; switch servers; check firewall and antivirus settings. |
| Internet works on some devices but not others | Device-specific issues | Restart devices; update network drivers; check for MAC address filtering on the router. |
| Wi-Fi connected but no internet access | ISP outage or DNS issues | Restart router; check ISP service status; change DNS servers; reset network settings. |
Taking proactive steps can enhance performance and prevent future issues.
Tips for Optimal Placement:
Why It Matters:
Proper placement maximizes signal strength and coverage, reducing dead zones and improving overall connectivity.
Wi-Fi Extenders:
Mesh Networks:
Why It Matters:
Extending your network eliminates weak spots, ensuring consistent connectivity throughout your space.
Essential Security Measures:
Why It Matters:
Securing your network protects personal information and prevents unauthorized access, which can slow down your network or lead to malicious attacks.
While many issues can be resolved independently, some situations require expert assistance.
Signs You Need Professional Help:
How to Choose a Professional:
Why It Matters:
A professional can diagnose and fix complex issues efficiently, saving you time and preventing further problems.
Staying connected is vital in our modern world. Network issues can be disruptive, but with the right knowledge and tools, you can resolve most problems yourself. This guide provides the foundation to troubleshoot effectively, understand the root causes, and optimize your network for the best performance.
Remember, technology should serve you, not hinder you. By taking proactive steps and knowing when to seek help, you can ensure a seamless and secure online experience.
Stay Connected, Stay Empowered
Keywords: Network troubleshooting, network issues, internet connection problems, slow internet, Wi-Fi issues, network optimization, DNS problems, network security, router placement, mesh networks.
Meta Description: Learn how to troubleshoot and resolve common network connection issues with our comprehensive guide. Discover solutions to slow internet, Wi-Fi problems, DNS errors, and more to keep you connected.
A: Slow internet after a restart could be due to bandwidth congestion from multiple devices, outdated hardware, or ISP-related issues like throttling. Check for background downloads on your devices, update your router’s firmware, and consider contacting your ISP to verify if there are service issues or if an upgrade is needed.
A: This situation often points to a problem between your router and the internet (WAN side). Try the following steps:
A: To boost your Wi-Fi signal:
A: If specific websites aren’t loading:
A: Wired connections (Ethernet) offer more stability and faster speeds compared to Wi-Fi. They are less susceptible to interference and are ideal for bandwidth-intensive activities like gaming or streaming in high definition.
A: Yes, neighboring Wi-Fi networks can cause interference, especially if they are on the same channel. Use a Wi-Fi analyzer tool to find the least congested channel and adjust your router settings accordingly.
A: Resetting your router can resolve persistent issues, but it will erase all custom settings, including your Wi-Fi network name and password. Ensure you have the necessary information to reconfigure your router before performing a factory reset.
A: Quality of Service (QoS) allows you to prioritize network traffic for specific applications or devices, ensuring they receive the necessary bandwidth. This is particularly useful for activities like gaming or video conferencing.
A: Limited connectivity means your device is connected to the network but cannot access the internet. This could be due to IP conflicts, DHCP issues, or problems with your ISP.
A: Connect a device directly to your modem using an Ethernet cable. If the issue persists, it’s likely an ISP problem. Additionally, you can check your ISP’s service status page or contact their support line.
Don’t let network issues slow you down. With the right tools and support, you can enjoy a seamless and secure connection. Explore our range of advanced networking products and services designed to meet your unique needs.
Empower your connection today. Let’s build a better network together!
Stay connected with confidence and ease. Remember, we’re just a click or call away whenever you need assistance. Happy networking!
Unlock the secrets of efficient networking by mastering CIDR, subnetting, and IP addressing. Dive deep into IP classes, learn how to calculate hosts, and discover the differences between DHCP and static IPs.

In today’s interconnected world, understanding networking concepts is essential for IT professionals, network engineers, and even tech-savvy individuals. Central to networking is the concept of IP addressing, which allows devices to communicate over the internet and local networks. This comprehensive guide will delve into CIDR and subnetting, demystifying these concepts and providing practical insights into IP address classes, host calculations, and the differences between DHCP and static IPs.
Whether you’re preparing for a certification, enhancing your networking knowledge, or seeking to optimize your network’s performance, this article will equip you with the necessary tools and understanding to navigate the complexities of IP addressing.
An Internet Protocol (IP) address is a unique numerical identifier assigned to every device connected to a computer network that uses the Internet Protocol for communication. Think of it as a postal address for your device, enabling data to be sent and received accurately.
An IP address serves two principal functions:
There are two versions of IP addresses in use today:
IPv4 Example: 192.168.1.1
IPv6 Example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
This guide will focus on IPv4, as it’s foundational for understanding CIDR and subnetting.
IPv4 addresses are traditionally divided into five classes (A to E), each serving different purposes.
1.0.0.0 to 126.255.255.255255.0.0.0128.0.0.0 to 191.255.255.255255.255.0.0192.0.0.0 to 223.255.255.255255.255.255.0224.0.0.0 to 239.255.255.255240.0.0.0 to 254.255.255.255Note: The address 127.0.0.1 is reserved for loopback testing and not assigned to any class.
Subnetting is the process of dividing a large network into smaller, more manageable sub-networks, or subnets. By breaking down a network, organizations can improve network performance and security.
Classless Inter-Domain Routing (CIDR) is a method for allocating IP addresses and routing that replaces the old system based on classes A, B, and C.
Introduced in 1993, CIDR allows for more efficient allocation of IP addresses by allowing variable-length subnet masks, effectively eliminating the rigid structure of classful addressing.
CIDR notation includes the IP address, followed by a slash (/) and a number indicating the number of bits in the network prefix.
Example: 192.168.1.0/24
/24 indicates that the first 24 bits are the network part, leaving 8 bits for host addresses.Understanding the Notation:
By adjusting the number after the slash, network administrators can create subnets of varying sizes to suit their needs.
To calculate the number of possible hosts in a subnet:
2^n - 2, where n is the number of host bits.Example:
/2432 - 24 = 82^8 - 2 = 254Why Subtract 2?
Let’s subnet a Class C network 192.168.1.0/24 into smaller subnets.
Objective: Create 4 subnets.
Step 1: Determine the Number of Subnets Needed
n such that 2^n >= S2^2 = 4 (So, we need 2 bits for subnetting)Step 2: Calculate the New Subnet Mask
11111111.11111111.11111111.0000000011111111.11111111.11111111.11000000255.255.255.192/26 (Since 24 + 2 = 26)Step 3: Calculate the Number of Hosts per Subnet
32 - 26 = 62^6 - 2 = 62Step 4: Determine the Subnet Addresses
256 - 192 = 64 (Based on the last octet of the subnet mask)192.168.1.0/26 (Hosts: .1 to .62)192.168.1.64/26 (Hosts: .65 to .126)192.168.1.128/26 (Hosts: .129 to .190)192.168.1.192/26 (Hosts: .193 to .254)Below is a comprehensive cheat sheet for CIDR notation, subnet masks, and the number of hosts per subnet.
| CIDR Notation | Subnet Mask | Total Hosts | Usable Hosts |
|---|---|---|---|
| /8 | 255.0.0.0 | 16,777,216 | 16,777,214 |
| /9 | 255.128.0.0 | 8,388,608 | 8,388,606 |
| /10 | 255.192.0.0 | 4,194,304 | 4,194,302 |
| /11 | 255.224.0.0 | 2,097,152 | 2,097,150 |
| /12 | 255.240.0.0 | 1,048,576 | 1,048,574 |
| /13 | 255.248.0.0 | 524,288 | 524,286 |
| /14 | 255.252.0.0 | 262,144 | 262,142 |
| /15 | 255.254.0.0 | 131,072 | 131,070 |
| /16 | 255.255.0.0 | 65,536 | 65,534 |
| /17 | 255.255.128.0 | 32,768 | 32,766 |
| /18 | 255.255.192.0 | 16,384 | 16,382 |
| /19 | 255.255.224.0 | 8,192 | 8,190 |
| /20 | 255.255.240.0 | 4,096 | 4,094 |
| /21 | 255.255.248.0 | 2,048 | 2,046 |
| /22 | 255.255.252.0 | 1,024 | 1,022 |
| /23 | 255.255.254.0 | 512 | 510 |
| /24 | 255.255.255.0 | 256 | 254 |
| /25 | 255.255.255.128 | 128 | 126 |
| /26 | 255.255.255.192 | 64 | 62 |
| /27 | 255.255.255.224 | 32 | 30 |
| /28 | 255.255.255.240 | 16 | 14 |
| /29 | 255.255.255.248 | 8 | 6 |
| /30 | 255.255.255.252 | 4 | 2 |
| /31 | 255.255.255.254 | 2 | 0 |
| /32 | 255.255.255.255 | 1 | 0 |
Note: Usable hosts exclude network and broadcast addresses.
Dynamic Host Configuration Protocol (DHCP) is a network management protocol used to automate the process of configuring devices on IP networks. DHCP allows devices to receive IP addresses and other network configurations automatically.
How DHCP Works:
Advantages of DHCP:
A static IP address is a fixed IP address manually assigned to a device, remaining constant over time.
When to Use Static IPs:
Advantages of Static IPs:
| Aspect | DHCP | Static |
|---|---|---|
| Configuration | Automatic | Manual |
| Management | Centralized via DHCP server | Requires individual configuration |
| IP Changes | IP addresses can change over time | IP addresses remain constant |
| Ease of Use | User-friendly for large networks | Time-consuming for large-scale deployments |
| Best For | General user devices (computers, smartphones) | Servers, network devices, and critical hosts |
Understanding CIDR and subnetting is crucial for efficient network management and IP address allocation. By mastering these concepts, network administrators can optimize network performance, enhance security, and ensure scalable network architecture.
Whether deploying a small office network or managing a large enterprise infrastructure, the principles of CIDR, subnetting, and IP addressing form the foundation of effective networking. Embracing both DHCP and static IP assignments where appropriate ensures devices are correctly configured, promoting seamless communication across the network.
Empower your networking skills by delving deeper into these concepts, and stay ahead in the ever-evolving world of technology.
A Comprehensive Guide to Managed IT Support, Network Cabling Services, and Cybersecurity
Introduction
In today’s digital landscape, businesses of all sizes rely heavily on technology to operate efficiently and stay competitive. Managed IT support, network cabling services, and robust cybersecurity measures have become essential components for ensuring seamless business operations. This guide explores the benefits of these services, the different types available, and how to choose the right provider for your business.
Benefits of Managed IT Services
Managed IT services offer numerous advantages for businesses, IT professionals, and entrepreneurs, including:
Importance of Network Cabling Services
A reliable network infrastructure is the backbone of any organization’s IT environment. Professional network cabling services ensure:
The Role of Cybersecurity
Cybersecurity is critical in protecting sensitive business data and maintaining customer trust. Key aspects include:
Types of Managed IT Services
Different managed IT services cater to various business needs:
Choosing the Right Service Provider
When selecting a provider for managed IT support, network cabling, and cybersecurity services, consider:
Conclusion
Investing in managed IT support, professional network cabling services, and robust cybersecurity is essential for businesses aiming to streamline operations, enhance efficiency, and protect against cyber threats. By partnering with a reliable service provider, you can focus on your core business activities while leaving the technical aspects to the experts. Select a provider that aligns with your business goals to ensure a successful and enduring partnership.
Benefits of Using Azure Active Directory Accounts for Users Within an Organization vs. Individualized Accounts
Implementing Azure Active Directory (Azure AD) accounts for users within your organization offers numerous advantages over individualized accounts. Here are the key benefits:
Conclusion
Using Azure AD accounts within your organization centralizes and strengthens user management and security. It not only streamlines administrative tasks but also enhances compliance, scalability, and overall user experience. In contrast, individualized accounts lack centralized control, making them less secure and more cumbersome to manage, especially as your organization grows.
If you’re looking to enable your office copier to send emails via Office 365, this comprehensive guide will walk you through the process. We’ll cover how to create an SMTP relay with authentication, configure DNS SPF records using your office IP address, and address device limitations such as character count restrictions on Canon copiers.
Modern office copiers often need to send scanned documents via email. Using Office 365 as your SMTP relay ensures secure and reliable email delivery. However, setting this up involves multiple steps, including DNS configuration, Office 365 settings, and copier configuration—especially considering limitations like character count restrictions on some devices.
Sender Policy Framework (SPF) records help prevent email spoofing by specifying which IP addresses are authorized to send emails on behalf of your domain.
Access your DNS management console and locate the existing SPF record for your domain. It usually looks like this:
v=spf1 include:spf.protection.outlook.com -all
Modify the SPF record to include your office’s public IP address:
v=spf1 ip4:Your.Office.IP.Address include:spf.protection.outlook.com -all
Replace Your.Office.IP.Address with your actual static IP.
Update the SPF record and save the changes. DNS propagation may take up to 48 hours, but it usually updates within a few hours.
To allow your copier to send emails through Office 365, you need to set up a connector in Exchange Online.
Conditional Access Policies add an extra layer of security by controlling how and when your copier can access Office 365 services.
Now that the backend is set up, configure your copier to use the SMTP relay.
yourdomain-com.mail.protection.outlook.com.25 (recommended for SMTP relay)Some Canon copiers have a 48-character limit for SMTP server addresses. If your MX record exceeds this limit:
[123.456.789.012].scanner@yourdomain.com.Setting up an SMTP relay for your copier with Office 365 enhances your organization’s ability to send emails securely. By carefully configuring DNS records, Office 365 connectors, conditional access policies, and copier settings—while accounting for device limitations—you can ensure seamless operation.
Remember: Always keep security in mind. Regularly update passwords and monitor access logs to maintain a secure environment.
Navigating multi-vendor IT environments is a common challenge for businesses seeking to leverage specialized solutions and best-of-breed technologies.
However, this approach often leads to complexity, fragmentation, and increased security risks.
This article will explore the common challenges businesses face in managing multi-vendor IT environments and provide solutions to streamline processes, enhance security, and optimize performance.
Relying on multiple IT vendors is a common practice for businesses seeking specialized solutions and flexible partnerships. However, this approach can quickly lead to a complex and fragmented IT environment, creating challenges that impact efficiency, security, and ultimately, the bottom line.
This multi-vendor IT dilemma requires careful consideration and strategic solutions to ensure your technology infrastructure supports your business goals.
The challenges are multifaceted and impact various aspects of business operations:
These challenges highlight the need for standardization and simplification in multi-vendor IT environments. By streamlining processes, consolidating systems, and implementing a more integrated approach, businesses can overcome these obstacles and unlock the true potential of their IT infrastructure.
Facing a multi-vendor IT environment that feels more like a tangled jungle than a well-oiled machine? While the challenges are real, so are the solutions.
By implementing strategic approaches and embracing a more integrated mindset, businesses can tame the chaos of multi-vendor IT and transform it into a source of efficiency, security, and growth.
Here are some key strategies for streamlining your multi-vendor IT environment:
Just as a common language facilitates communication, standardizing IT processes, systems, and technologies across vendors can significantly reduce complexity and improve efficiency.
This might involve adopting a common platform for communication, implementing standardized security protocols, or utilizing a centralized management system for monitoring and managing all your IT assets.
Automation is a powerful tool for streamlining repetitive tasks, reducing human error, and freeing up your IT team to focus on more strategic initiatives.
Automating tasks such as software updates, security patching, and data backups can significantly enhance efficiency and reduce the risk of oversights.
A centralized management platform provides a single pane of glass for monitoring and managing your entire IT environment, regardless of the vendor.
This allows you to gain a holistic view of your systems, identify potential issues proactively, and streamline troubleshooting and support processes.
A well-designed and implemented structured cabling system provides a solid foundation for your IT infrastructure, ensuring reliable connectivity, efficient data flow, and scalability for future growth.
This is particularly important in multi-vendor environments, where different systems need to communicate seamlessly.
Partnering with a Managed Service Provider (MSP) like LayerLogix can be a game-changer for businesses struggling with multi-vendor IT.
MSPs offer expertise in managing complex IT environments, providing 24/7 support, proactive monitoring, and strategic guidance to optimize your systems, enhance security, and reduce costs.
A robust disaster recovery plan is essential for any business, but it’s particularly crucial in multi-vendor environments, where the complexity of systems can increase the risk of downtime and data loss.
A well-defined plan ensures business continuity in the event of an unforeseen event, minimizing disruption and enabling a swift recovery.
By embracing these strategies, businesses can transform their multi-vendor IT environments from a source of frustration into a foundation for efficiency, security, and growth.
LayerLogix can guide you through this transformation, providing the expertise, tools, and support you need to streamline your IT operations and unlock the true potential of your technology infrastructure.
Businesses today rely on a diverse range of IT vendors to meet their specific needs, from specialized software solutions to cloud services and infrastructure support.
While this multi-vendor approach offers flexibility and access to best-of-breed technologies, it also creates inherent complexities in managing disparate systems, ensuring seamless integration, and maintaining a robust security posture.
LayerLogix recognizes these challenges and acts as a strategic partner for businesses seeking to simplify and secure their multi-vendor IT environments. We provide a comprehensive suite of Managed IT services designed to streamline operations, enhance security, and optimize IT performance across all vendor platforms.
We offer centralized management and monitoring, providing a holistic view of your IT infrastructure and enabling proactive issue resolution. Our streamlined support processes eliminate the need to juggle multiple vendor support lines, simplifying communication and ensuring timely resolution of any IT challenges.
As your business grows and your IT needs evolve, we’ll work with you to scale your IT infrastructure seamlessly.
Partnering with LayerLogix transforms your multi-vendor IT environment from a potential source of complexity and vulnerability into a streamlined, secure, and efficient foundation for your business’s success.
We’ll handle the technical intricacies, so you can focus on what matters most – achieving your business goals.
A fragmented, multi-vendor IT environment can feel like a ticking time bomb, threatening to disrupt operations, compromise security, and drain resources. Juggling disparate systems, navigating conflicting vendor communication, and struggling to maintain a cohesive security posture can leave businesses feeling overwhelmed and vulnerable.
But there’s a better way.
A survey conducted by PMI India’s Excellence Enablers Forum (EEF) among practitioners in IT organizations in India revealed that project management in a multi-vendor environment is one of the topmost challenges faced by businesses.
The study highlighted several key pain points, including unclear business goals, poor integration between vendors, lack of team bonding, friction due to skill gaps, communication breakdowns, fluid scope boundaries, ineffective governance processes, non-standard environments, and a lack of standard compliance frameworks.
These challenges underscore the need for a more integrated and collaborative approach to multi-vendor IT management.
By breaking down silos, streamlining processes, and consolidating systems, businesses can achieve:
LayerLogix’s expertise in integrating and optimizing multi-vendor systems can help you achieve this transformation. We’ll work closely with you to understand your unique needs, develop a customized IT roadmap, and implement solutions that streamline your operations, enhance security, and empower your business to thrive in the digital age.
Don’t let the complexity of multi-vendor IT hold your business back.
Embrace the transformative power of integrated IT solutions and unlock a new level of efficiency, security, and growth.
Contact LayerLogix today to discuss how we can help you simplify your IT landscape and achieve your business goals.
Clipboard Hijacking and How to Prevent It
Introduction
Clipboard hijacking is a type of cybersecurity threat where an attacker gains access to the data copied to your clipboard. This can include sensitive information like passwords, credit card numbers, or personal identification details. Clipboard hijacking often occurs when malicious code is introduced to your system through a compromised website, software, or browser extension. Once an attacker gains access to your clipboard, they can replace its content with their own or retrieve data for malicious purposes. In this article, we will discuss how clipboard hijacking works and provide steps on how to prevent it.
Clipboard hijacking generally exploits vulnerabilities in web browsers or software with clipboard access. Here’s a typical process:
The good news is that clipboard hijacking can be prevented with some basic precautions. Here’s how to protect yourself:
One of the main methods attackers use is exploiting vulnerabilities in your web browser. By using a secure, up-to-date browser like Google Chrome, Mozilla Firefox, or Microsoft Edge, you significantly reduce the risk. These browsers regularly update their security protocols to protect against clipboard hijacking attempts.
Most browsers allow websites to access your clipboard automatically, but this feature can be turned off. Here’s how to disable it:
Settings > Privacy and Security > Site Settings > Clipboard.about:config in the address bar.dom.event.clipboardevents.enabled and toggle it to false.Malware often enters a system through shady software or browser extensions. Install only trusted, well-reviewed applications and browser extensions.
A reliable antivirus program can detect and block malicious scripts that attempt to hijack your clipboard. Look for an antivirus solution that provides:
Some popular options include Bitdefender, Norton, and Kaspersky.
Be vigilant about the data you copy to your clipboard. If you notice anything unusual, such as unfamiliar text or numbers appearing in your clipboard after you copy something, this could be a sign of clipboard hijacking.
Certain apps and browser extensions clear clipboard data after a few seconds to prevent hijacking. You can use these tools to ensure your sensitive information isn’t left on the clipboard for too long.
It’s always a good idea to minimize the amount of sensitive data copied to your clipboard. Avoid copying sensitive information like passwords or credit card numbers unless absolutely necessary.
Some clipboard hijacking attacks exploit administrative privileges on your system. By limiting your account’s access level and running applications with the fewest privileges, you can reduce the risk of clipboard hijacking.
Clipboard hijacking may seem like a minor threat, but it can have significant consequences if sensitive data falls into the wrong hands. By following these steps, you can secure your clipboard from attackers and ensure that your sensitive information remains safe. Stay vigilant, maintain strong security practices, and regularly review your system for any signs of hijacking attempts.
Managed IT services are a strategic investment for businesses seeking to future-proof their IT infrastructure.
This article explores how partnering with a Managed Service Provider (MSP) like LayerLogix can empower small and mid-sized industrial organizations to navigate the complexities of modern IT, enhance security, drive innovation, and build a foundation for long-term growth.
Small and mid-sized industrial organizations face a critical challenge in today’s rapidly changing technological landscape. Their IT infrastructure, the backbone of their operations, must be agile and adaptable to keep pace with innovation and maintain a competitive edge.
Failing to future-proof IT can lead to a cascade of problems, impacting everything from productivity and security to innovation and customer satisfaction.
Outdated systems and slow networks can cripple a company’s efficiency, hindering workflows and leading to costly downtime. The financial impact can be staggering, with a recent study finding that “the average cost of downtime across all industries has historically been about $5,600 per minute, but it has grown to about $9,000 per minute.”
Worse yet, aging infrastructure becomes a magnet for cybercriminals seeking vulnerabilities to exploit.
Furthermore, a stagnant IT infrastructure stifles innovation. It’s unable to support the new technologies that drive efficiency and agility, hindering a company’s ability to compete in the marketplace.
So how can businesses overcome these challenges and build an IT infrastructure ready to face the future?
Enter managed IT services.
Companies gain a crucial advantage by partnering with a managed service provider like LayerLogix. A 2023 report by MarketsandMarkets reveals that businesses outsourcing their IT to managed service providers (MSPs) can save up to 40% on IT-related costs compared to maintaining an in-house IT team.
This cost efficiency frees up resources to be invested back into innovation and growth.
By leveraging managed IT services, businesses can build a future-proof foundation and focus on their core strengths – driving innovation and achieving operational excellence.
Small and mid-sized industrial organizations, spanning manufacturing, healthcare, and energy sectors, operate in demanding environments where efficiency, security, and reliability are paramount.
Managed IT services offer a strategic advantage, empowering these businesses to overcome IT challenges and unlock their full potential.
One of the most significant benefits of managed IT services is their ability to streamline IT processes. Instead of juggling multiple vendors, contracts, and support requests, businesses can rely on a single provider for all their IT needs.
A 2022 survey by CompTIA found that 78% of organizations that use MSPs reported improved efficiency and productivity in their IT operations. This streamlined approach frees up internal resources to focus on core business activities, boosting overall productivity.
Managed IT services play a crucial role in enhancing cybersecurity. MSPs are at the forefront of the cybersecurity landscape, staying ahead of evolving threats and implementing robust security measures.
Organizations partnering with MSPs experience a significant reduction in cyber risk, with a 2024 report by the International Data Corporation (IDC) finding a 42% reduction in successful cyberattacks compared to those with in-house IT teams.
This enhanced security posture safeguards sensitive data, protects against costly breaches, and ensures compliance with industry standards.
Managed IT services also provide scalability and flexibility, allowing businesses to adapt quickly to changing demands. As a company grows, its IT infrastructure needs to evolve.
This adaptability is critical for seizing new opportunities and remaining competitive in dynamic markets.
This expertise helps businesses mitigate risk, avoid costly penalties, and protect their reputation.
By leveraging managed IT services, small and mid-sized industrial organizations can build a strong foundation for growth, innovation, and success.
The combination of streamlined processes, enhanced security, scalability, and compliance makes managed IT services a strategic investment for businesses striving to navigate the complexities of the modern technological landscape.
While the benefits of partnering with a Managed Service Provider (MSP) are clear, understanding what specifically is included in “Managed IT Services” can often feel like navigating a maze of technical jargon. This section will unpack the core services and tailor them to the needs of small and mid-sized industrial organizations.
Think of Managed IT Services as a comprehensive toolkit, equipped with the tools and expertise needed to optimize your IT infrastructure, strengthen your security, and empower your growth. Here’s a breakdown of some essential components:
The specific mix of services will be tailored to each organization’s unique needs and industry, creating a flexible and adaptable solution that empowers growth and innovation.
The IT landscape is in a constant state of evolution, driven by groundbreaking innovations and the ever-increasing demands of the digital world.
For small and mid-sized industrial organizations, staying ahead of the curve is no longer a luxury – it’s a necessity for survival and growth.
Here are some key trends shaping the future of IT infrastructure:
Cloud computing has become a cornerstone of modern IT, offering scalability, flexibility, and cost-effectiveness that traditional on-premises infrastructure struggles to match.
For industrial organizations, this means access to powerful cloud-based platforms for data analytics, machine learning, Industrial IoT, and more.
As data generation explodes, particularly in industrial settings with sensor-laden equipment and interconnected devices, processing data closer to its source is becoming crucial.
Edge computing, which brings computation and data storage closer to the “edge” of the network, minimizes latency, improves real-time decision-making, and optimizes bandwidth usage.
Cyber threats are growing increasingly sophisticated, targeting vulnerabilities in industrial control systems, supply chains, and connected devices.
Staying ahead of these threats requires a proactive approach to security, with robust defenses, continuous monitoring, and expert incident response capabilities.
Artificial intelligence and automation are revolutionizing IT management, enabling more efficient operations, proactive issue resolution, and enhanced security. AI-powered tools can analyze vast amounts of data, identify anomalies, predict potential failures, and automate routine tasks, freeing up IT staff to focus on strategic initiatives.
Navigating this complex landscape can be daunting, but managed IT services provide a strategic advantage.
By partnering with a trusted MSP like LayerLogix, businesses gain access to:
The future of IT infrastructure is dynamic and full of exciting possibilities.
By partnering with LayerLogix, businesses can navigate this evolving landscape with confidence, building a future-proof foundation for growth and innovation.
Don’t get left behind. Contact LayerLogix today and explore how we can help you harness the power of emerging technologies and safeguard your IT infrastructure for the future.
In today’s fast-paced business environment, small and mid-sized businesses (SMBs) face the daunting challenge of keeping up with technological advancements while managing limited resources.
Managed IT services have emerged as a strategic solution that allows SMBs to leverage expert IT support without the overhead associated with maintaining a full-time, in-house IT staff.
Here we explore how managed IT services can transform your business operations, offering improved efficiency, cost savings, and robust data protection.
One of the most significant advantages of managed IT services is the ability to predict and control IT expenses. Traditional approaches to IT management often involve unexpected costs due to emergency repairs, software upgrades, or hardware failures.
Managed service providers (MSPs), on the other hand, offer their services for a monthly flat fee. This subscription-based model provides businesses with predictable budgeting, allowing them to plan their finances more effectively and allocate resources where they’re needed most.
This is especially helpful for small and mid-sized businesses that don’t have massive budgets with expanded capabilities to absorb unplanned expenses.
For SMBs, building an in-house team with diverse and comprehensive technical expertise can be prohibitively expensive. Managed IT services give businesses access to a pool of professionals who are well-versed in various areas of technology. These experts stay on top of the latest trends and developments in the tech world, ensuring that your business benefits from cutting-edge solutions.
With managed IT services, the provider is in charge not only of guaranteeing quality and effectiveness but also of training its professional teams to deliver increasingly superior services over time.
Whether it’s cybersecurity, cloud computing, or network management, MSPs bring a wealth of knowledge that can help drive your business forward.
Data breaches can have devastating consequences for businesses of any size but pose an even greater threat to SMBs that may lack robust security measures. MSPs specialize in implementing multi-layered security strategies tailored to protect sensitive information from cyber threats.
With continuous monitoring and regular updates to security protocols, managed service providers ensure that your data remains secure against evolving threats. And doing so on a daily basis, in the context of being specialized, they are enabled to deliver superior results.
Continuing from the solid foundation of predictable IT budgeting, access to expertise, and strengthened data protection, managed IT services offer additional layers of value that can be pivotal for small and mid-sized businesses.
Managed IT services are not just about outsourcing support; they’re a strategic move that can lead to significant cost reductions. By partnering with an MSP, businesses can avoid the capital expenditure associated with setting up an in-house IT infrastructure.
This includes savings on hiring costs, training, benefits, and office space. Moreover, MSPs can achieve economies of scale by serving multiple clients, which translates into lower operational costs for your business.
Keeping track of software licenses, hardware lifecycles, and vendor contracts can be overwhelming for SMBs. Managed service providers take on the responsibility of managing your IT assets efficiently. They ensure that software is up-to-date and compliant with licensing requirements.
Hardware is maintained or upgraded before it becomes obsolete or fails—minimizing downtime and keeping your business running smoothly.
Managed service providers offer comprehensive support that goes beyond fixing immediate problems. They work proactively to identify potential issues before they impact your operations. With 24/7 monitoring and helpdesk services, MSPs provide fast response times to any technical difficulties you may encounter. This level of support ensures minimal disruption to your business activities and enhances overall productivity.
Furthermore, MSPs often use advanced remote management tools that allow them to resolve many issues without needing to visit your site physically. This remote troubleshooting capability not only speeds up resolution times but also extends the reach of your IT support—no matter where in the world your team may be working from.
Managed IT services are inherently scalable, allowing businesses to adjust their level of service based on current needs and future growth. As your business expands, so too can your IT support without the need for significant capital investment or delays in recruitment. This flexibility is crucial for SMBs that experience seasonal fluctuations or are on a fast growth trajectory.
Every business has its own set of challenges and requirements when it comes to technology. MSPs recognize this diversity and often provide customized solutions that align with specific business goals and industry standards. Whether you need specialized software support, industry-specific compliance assistance, or strategic IT planning, a managed service provider can tailor their offerings to fit your exact needs.
With an MSP taking care of your IT infrastructure, your team is free to focus on what they do best—growing the business. This shift away from troubleshooting tech issues allows for better allocation of human resources towards core functions such as sales, customer service, and product development.
Managed service providers do more than just manage day-to-day IT operations; they also serve as strategic partners in planning for the future. They help businesses anticipate technological trends and make informed decisions about investments in new technologies. With their expertise at your disposal, you can develop a long-term IT strategy that supports sustainable growth.
Then we have data insights for better decision-making. A key aspect of managed IT services is the ongoing evaluation of performance metrics and regular reporting back to the client. These reports provide insights into system performance, security posture, and user activity—enabling continuous improvement in processes and policies.
Perhaps one of the most valuable aspects of engaging with an MSP is the partnership that develops over time. As they become more familiar with your business operations, MSPs can offer increasingly insightful recommendations that drive efficiency and innovation.
In conclusion, small and mid-sized businesses stand to gain significantly from managed IT services—from predictable budgeting to expert guidance on long-term strategy. By partnering with an MSP like LayerLogix, you not only ensure that your technology needs are met but also position your business for success in an increasingly digital world.
LayerLogix offers a comprehensive suite of managed IT services designed specifically for SMBs looking to optimize their operations while maintaining robust security measures.
Contact us today to learn how we can help transform your business’s approach to technology management.
MSI errors 2503 and 2502 are common installation errors that occur during the process of installing or uninstalling software on Windows operating systems. These errors usually indicate that the installer is unable to complete its task due to a problem with permissions or file access. Error 2503 occurs when there is a problem with the installer’s permissions, while error 2502 is related to file access issues.
Various factors, including corrupted files, outdated software, or insufficient user privileges can cause both of these errors. To solve these errors, users can try several troubleshooting steps such as running the installer as an administrator, disabling antivirus software temporarily, or performing a clean boot.
MSI error 2502 is a common issue that occurs during the installation or uninstallation of software in Windows. It generally arises due to corrupt or incomplete installation files, outdated drivers, or conflicts with other software. To fix the problem, you can try several solutions such as running the installer as an administrator, clearing temporary files, disabling antivirus software temporarily, updating drivers and operating system, and repairing registry entries.
Additionally, you can also use third-party tools like CCleaner to clean up your system and remove any unwanted files that may be causing the error. By following these steps carefully, you can resolve MSI error 2502 and ensure smooth software installations on your Windows computer.
Check the user permissions of C:\Windows\Temp and ensure the current user has full access to that folder as well as TrustedInstaller and Administrative accounts on the network.
To prevent future occurrences of MSI error 2503 and 2502, it’s important to maintain a clean and organized computer system. Regularly cleaning up temporary files, removing unnecessary programs, and updating drivers can help prevent errors from occurring.
It’s also essential to be cautious when installing new software or updates. Make sure you’re downloading the software from a trusted source and that your computer meets the program’s system requirements.
Another way to prevent errors is to run regular scans for viruses and malware. Malicious software can cause various issues with your computer, including MSI errors.
By following these preventative measures, you can reduce the likelihood of experiencing MSI error 2503 and 2502 in the future.
SNMP TL;DR Takeaways:
In the vast realm of computer networks, efficient management is crucial for smooth operations and troubleshooting.
This is where Simple Network Management Protocol (SNMP) steps in as a reliable ally.
SNMP is like the conductor of an orchestra, coordinating and monitoring the performance of network devices. Let’s dive into the world of SNMP, exploring its applications, distinguishing it from SMTP, and uncovering whether it dances to the tune of TCP or UDP.
SNMP, the unsung hero of network management, serves as a bridge between network management systems and devices. It ensures a seamless exchange of information by acting as a communication protocol.
The Simple Network Management Protocol tirelessly roams the network landscape, much like a messenger, collecting valuable data from devices and conveying it back to the management system.
SNMP enables administrators to monitor bandwidth usage, detect anomalies, and perform remote configuration changes. It serves as the eyes and ears of the network, providing real-time insights into device performance, error notifications, and configuration details.
By harnessing the power of the Simple Network Management Protocol, administrators can proactively manage their networks, troubleshoot issues efficiently, and ensure optimal performance.
The SNMP architecture consists of three essential components. The managed devices, including routers, switches, and servers, form the actors on the network stage.
Agents, embedded within these devices, act as intermediaries, collecting and forwarding data to the management systems.
Lastly, the network management systems orchestrate the Simple Network Management Protocol symphony, analyzing the received data, generating reports, and issuing commands to the managed devices.
This symbiotic relationship ensures that network administrators have a comprehensive overview of their network’s health and can take informed actions accordingly.
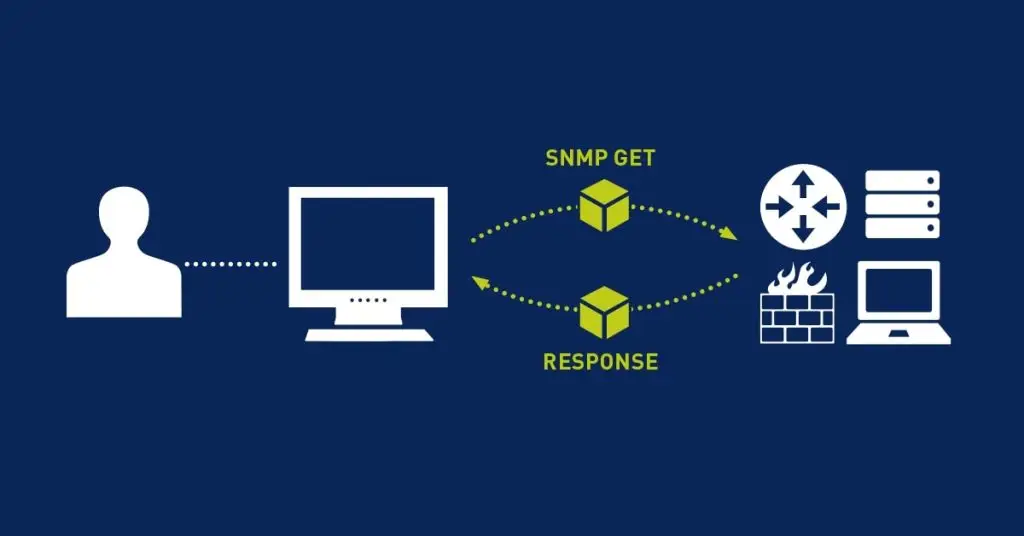
Though SNMP and SMTP may appear similar due to their acronymic resemblance, they serve distinct purposes in the realm of networking. SNMP focuses on network management, while SMTP stands for Simple Mail Transfer Protocol, primarily used for email transmission.
To draw a comparison, let’s imagine SNMP as a diligent janitor, meticulously monitoring and managing the network’s cleanliness and functionality. On the other hand, SMTP resembles a dedicated postman, ensuring the smooth delivery of electronic mail across networks.
While the Simple Network Management Protocol keeps a watchful eye on the network’s health, SMTP ensures that your emails traverse the vast digital landscape, reaching their intended recipients promptly.
Both SNMP and SMTP play vital roles in their respective domains, contributing to efficient management and seamless communication within networks.
Understanding their differences allows network administrators to leverage the right protocol for the task at hand, ensuring smooth operations and reliable information exchange.
In the vast world of networking, protocols dictate the rules of engagement between devices. When it comes to SNMP, it chooses to dance to the tune of UDP (User Datagram Protocol) rather than TCP (Transmission Control Protocol).
UDP, known for its speed and simplicity, can be likened to a quick messenger that delivers messages or “datagrams” between devices without the need to establish a persistent connection.
The Simple Network Management Protocol leverages the connectionless nature of UDP to efficiently transmit information from managed devices to the network management system.
However, this choice comes with trade-offs. UDP lacks built-in error checking and reliability mechanisms present in TCP. But fear not! SNMP compensates for this by incorporating error detection and recovery mechanisms within its protocol design.
It allows to provision of a reliable and efficient method of data exchange while benefiting from the speed and simplicity offered by UDP.
In the vast landscape of network management, Simple Network Management Protocol (SNMP) stands tall as a reliable and versatile protocol.
Its ability to monitor and control network devices empowers administrators to maintain optimal network performance and troubleshoot issues efficiently.
So embrace it, unravel its power, and orchestrate your network’s success.
IP Blacklist TL;DR Takeaways
Discover what an IP blacklist is, how your IP can get blacklisted, how to remove your IP from a blacklist, and learn the steps to blacklist an IP address. Stay informed and protect your network from malicious activities.
IP blacklist refers to the practice of filtering out illegitimate or malicious IP addresses from accessing your networks. It involves creating lists, commonly referred to as blacklists, that contain ranges or individual IP addresses you want to block.
These blacklists are implemented in conjunction with firewalls, intrusion prevention systems (IPS), and other traffic filtering tools. By utilizing blacklists, you can effectively filter out malicious traffic based on policies or by manually adding IP addresses.
Network security tools equipped with blacklisting capabilities can also automatically update and block newly identified malicious IP addresses.
IP blacklisting acts as a robust defense mechanism to protect your network from potential threats.
Understanding how your IP can end up on a blacklist is crucial to maintaining network security.
Attackers have devised various methods to circumvent blacklisting measures, making it important to stay vigilant. Here are some common ways your IP address can get blacklisted:
Finding your IP address on a blacklist can be a concerning discovery, but there are steps you can take to rectify the situation.
Here’s a guide to help you remove your IP from a blacklist:
By following these steps and maintaining a strong security posture, you can successfully remove your IP address from a blacklist and protect your network’s reputation.
Knowing how to blacklist an IP address can empower you to proactively defend your network against potential threats. Here’s a simple guide to help you blacklist an IP address:
By following these steps, you can leverage IP blacklisting as a potent defense mechanism and fortify your network’s security.
As cyber threats continue to evolve, implementing robust security measures is essential to safeguarding your network. IP blacklisting serves as a proactive defense mechanism against illegitimate or malicious IP addresses.
By understanding the concept of IP blacklisting, how IPs end up on blacklists, and the steps to remove or blacklist an IP address, you can effectively protect your network from potential threats.